Abracadabra $1.8m hack repeats earlier fork flaw, Hacken reveals
DeFi protocol Abracadabra lost $1.8 million after an attacker exploited a simple logic mistake in its batch function. Analysts at Hacken say the attacker already laundered funds via Tornado Cash.
- Abracadabra lost almost $2 million after an attacker exploited a simple logic mistake in its batch function, similar to an attack on a forked project days earlier.
- The attacker bypassed a safety flag meant to check if borrowers had enough collateral and drained six Cauldrons in one go before swapping the stolen MIM for ETH and routing it through Tornado Cash.
- This isn’t the first time Abracadabra’s code has been targeted, but the incident highlights how a small unimplemented function can let hackers take advantage, even when the same flaw was visible in a fork.
In early October, Abracadabra, a DeFi lending protocol that lets people borrow its stablecoin MIM using deposited tokens as collateral and suffered multiple hacker attacks before, this time once again lost about $1.8 million after an attacker used a simple logic mistake in the protocol’s batch function to borrow without putting up any collateral, in the same way a forked project had been hit just days before, analysts at blockchain security firm Hacken said in a research note shared with crypto.news.
Abracadabra launched as a way for people to use interest-bearing tokens as collateral and borrow a U.S. dollar-pegged token called Magic Internet Money, or MIM. The system is built around two pieces: Cauldrons, which handle the borrowing rules, and DegenBox, the shared vault that actually holds tokens. In short: you put up collateral in a Cauldron, and the DegenBox keeps track of the money behind the scenes.
The short version of what went wrong is this: a safety flag that’s supposed to force a final check on whether a borrower actually has collateral got turned off inside a single transaction. As Hacken’s report lays out, the attacker “exploited a logic flaw in Abracadabra’s cook() function where they could borrow MIM tokens and then immediately reset the validation flag that was supposed to check if they had enough collateral.” That allowed a one-shot, uncollateralized borrow across multiple Cauldrons.
Under the microscope
Here’s how the flow worked, in plain terms. Abracadabra uses a batched function called cook() so users can do several actions in one transaction. Say, deposit collateral and borrow in the same click. One of those actions, like the “borrow” step, sets a flag named needsSolvencyCheck to true, meaning “at the end of this transaction, check that the borrower is safe.”
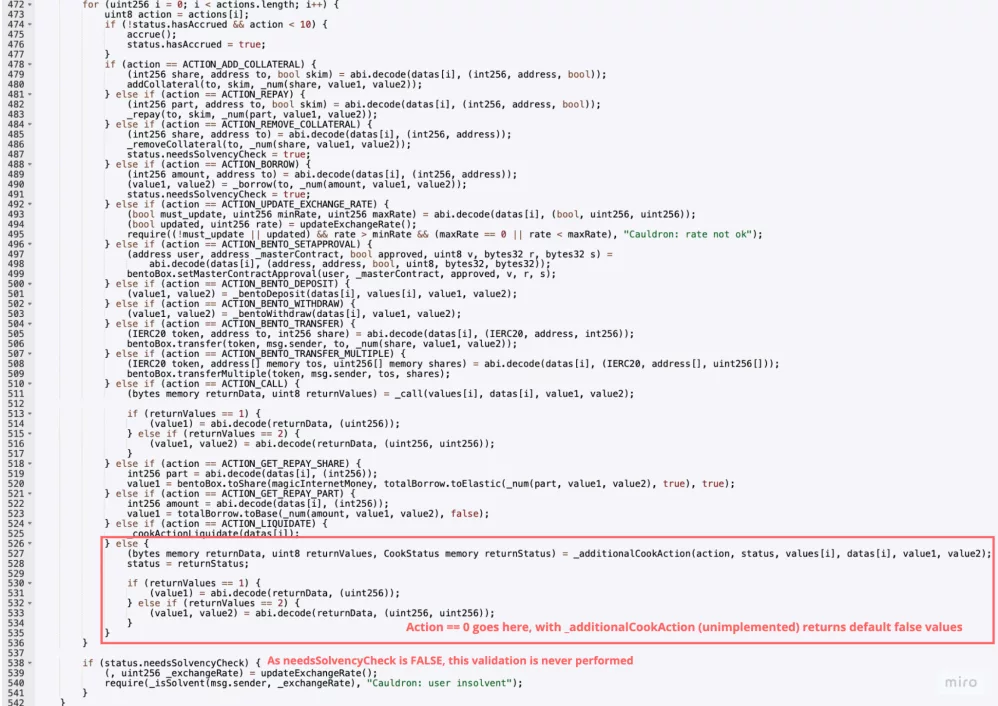
But another action that can be run inside the same batch calls “_additionalCookAction(…).” As Hacken points out, that function was declared as “virtual” and never was implemented, so by default it returned an empty object where everything was set to false, including that needsSolvencyCheck flag.
As a result, the attacker called the borrow action, then called the default action that reset the flag, and at the end, the protocol never checked solvency.
The analysts say the attacker hit six Cauldrons in one go, taking roughly 1.79 million MIM and swapping it for ETH. Attackers exploited vulnerability, and systematically went through six different Cauldrons and drained each one “using the same technique with a dedicated cook function call,” the analysts explained.
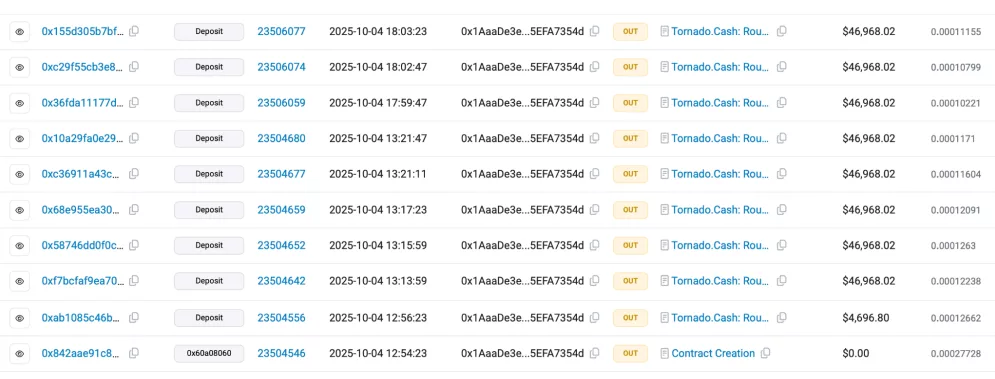
After swapping, the attacker routed funds through Tornado Cash, a crypto mixing protocol, mostly 10 ETH each, sending gradually over the following day.
And this isn’t the first time Abracadabra’s CauldronV4 code has been involved in trouble. Other incidents earlier this year used different edge cases in the same family of contracts. What’s interesting now is how fast the forked deployment reacted.
According to the report, a fork called Synnax paused or un-whitelisted its CauldronV4 master on its own DegenBox days before the Abracadabra drain, so basically the fork team pulled the emergency brake after spotting the same weak pattern, suggesting that the risk was visible to teams watching the code, if not fixed.
You May Also Like

Shiba Inu Faces Growing Risks as Leadership Instability Concerns Holders

Vitalik: Staking means defending the blockchain, and there will inevitably be resistance when exiting
